Python 2 will go end of life on 01 Jan 2020
Quick Public Safety Announcement, Python 2.7 goes end of life 01 Jan 2020. This is the end of the road for Python 2.x – there won’t be a version 2.8.
This means any Python code that’s still on 2.x needs updating to Python 3. Any code that isn’t moved over won’t receive security updates so will inevitably become insecure.
Identify your code
If you’ve got a lot of code it’s worth taking the time to check what’s where and which version of Python it’s using.
Python 3 was released at the end of 2008. Adoption has been slow, a factor has been that all of your dependencies need to support Python 3 before you can. Now that we’re over 10 years down the road this is much less likely to be an issue.
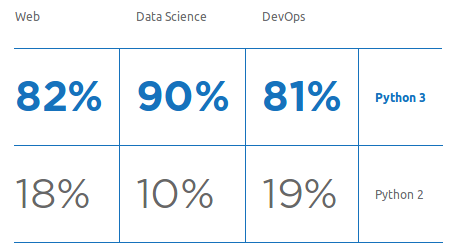
You can start off by checking code that has been written more recently. Hopefully this will have been written for Python 3. A survey by JetBrains shows that between 2017 and 2018 the number of developers that mostly used Python 2 fell from 25% to just 16%. It’s also interesting to note the divide between use cases. Data science having better adoption than both web and dev-ops.
Don’t forget old code
Unfortunately the numbers above are for code that developers are writing now. We’re also concerned with code that was written many years ago and hasn’t recently had any major changes. Looking at the number of packages downloaded instead of what developers are mostly using gives a different picture. The numbers are closer to 50/50 with the trend between data science and dev-ops still clear. TensorFlow is most often downloaded for Python 3 whilst botocore is heavily Python 2. Boto is heavily used in API access to cloud providers such as AWS.
If all of your recent code is Python 3 it’s worth having a good dig around for places old code might be hiding.
What are the steps to update to Python 3?
- The first step to update code is to make sure any packages you’re using support Python 3. A tool such as caniusepython3 should show you where the issues are.
- After that depending on the complexity of your code you can update it by hand or use a tool such as Futurize to help with the conversion .
A key part of smoothly updating is to have a good testing process so you can quickly find and fix the bits that unexpectedly break. See the porting guide for more info.
Feature image by See1,Do1,Teach1 licensed CC BY 2.0.



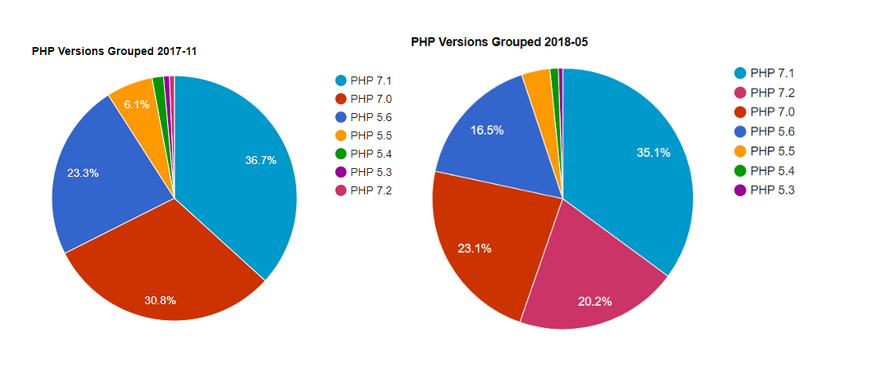 Upgrade from PHP 7.1 before the 1st December 2019.
Upgrade from PHP 7.1 before the 1st December 2019.